Privacy on Mastodon
Not sure what Mastodon is? Read Meet Mastodon first.
Before you start posting all of your inner thoughts to Mastodon, let’s discuss its privacy controls. Mastodon’s privacy controls are more robust and granular than those of Twitter. However, the distributed model and open source code means that privacy works a bit differently.
On Twitter, you either have a locked/protected account or a public account. With Mastodon there are two separate privacy controls: account locking and post privacy.
Locking your account prevents just anyone from following you and viewing your followers-only posts. Keep in mind that your public and followers-only posts are copied to the instances of your followers. Locking your account helps ensure that you have some awareness of where your posts will be redistributed.
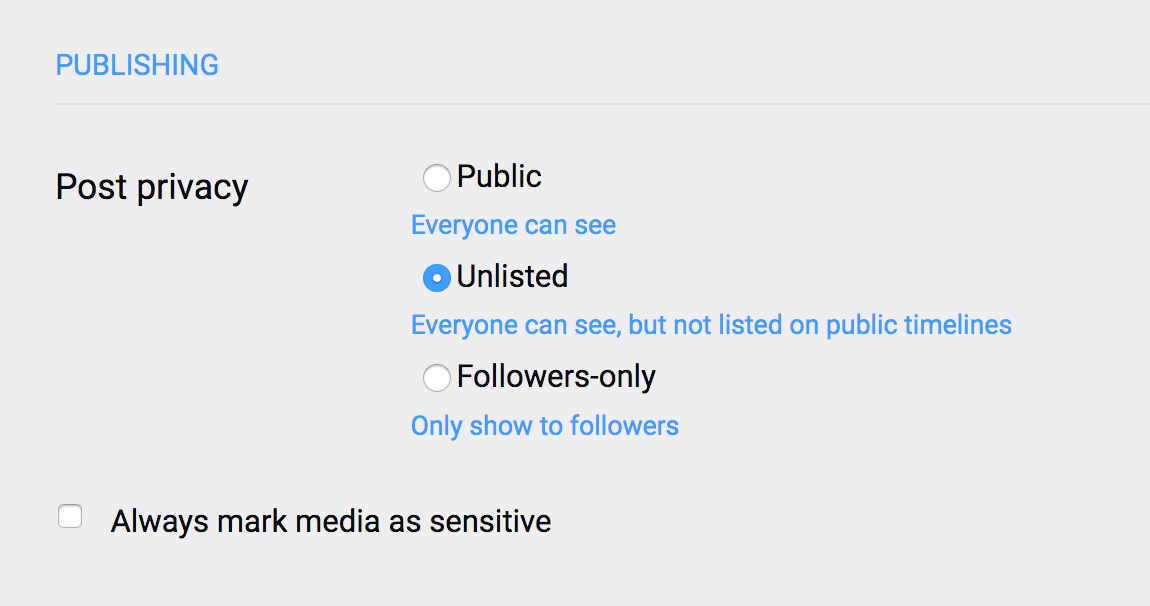
To mimic Twitter’s protected account feature, you must also set your default post privacy level to Followers-only (Edit profile → Preferences). You can override this setting for individual toots.
Reminder: even if your account is locked and you limit post visibility to followers, malicious users or instances can make those settings moot. Screen shots, changes to code, or a database breach can spill your secrets all over the internet. Standard internet sharing rules apply.
Impersonation concerns
User names are unique to each instance, not to Mastodon as a whole. As a result, impersonation is a real concern. Running an instance under your own (sub-)domain may be the best way to insulate yourself and others. Your Mastodon identity would then be tied to some other piece of information that’s connected to you.
How does this relate to privacy? Well, impersonation becomes a problem when you accept a follower request. A new request from yourhomie@toot.cafe should put you on guard, since it may not be from the same person as yourhomie@mastodon.xyz. You could be getting catfished, and sending direct messages to a stranger or giving them access to your protected posts.
Mastodon accounts are a bit like email addresses. jane.jones@gmail.com may not be the same Jane Jones who uses jane.jones@hotmail.com. She may not be the Jane Jones you know. She may not be “Jane Jones” at all. Take a moment to verify follower requests that look like they're from people you know.
Because Mastodon is a decentralized network, there’s not much recourse against impersonators. With Facebook, Twitter, and Instagram, you can try to inform the company that an account is indeed a fake and should be deactivated.
With Mastodon, you can try to plead your case to the moderators and administrators of the impersonator’s instance. But if the instance administrator is the impersonator, you’re out of luck. Mastodon admins can isolate the impersonating instance and prevent it from federating with their instances. But that may not keep the impersonator out of search engine results.
Of course, avoiding Mastodon also doesn't prevent impersonation. Nor is impersonation a problem that's unique to Mastodon.
Trumpet sound courtesy of profcalla.
This is the second of a three-part series. Part 1 is Meet Mastodon. Part 3 looks at Mastodon Tools.